Behind The Scenes
All we get in this challenge is one file titled behindthescenes executing it prompts for a password.
chmod +x behindthescenes
./behindthescenes
./challenge <password>
./behindthescenes something
<NO OUTPUT>
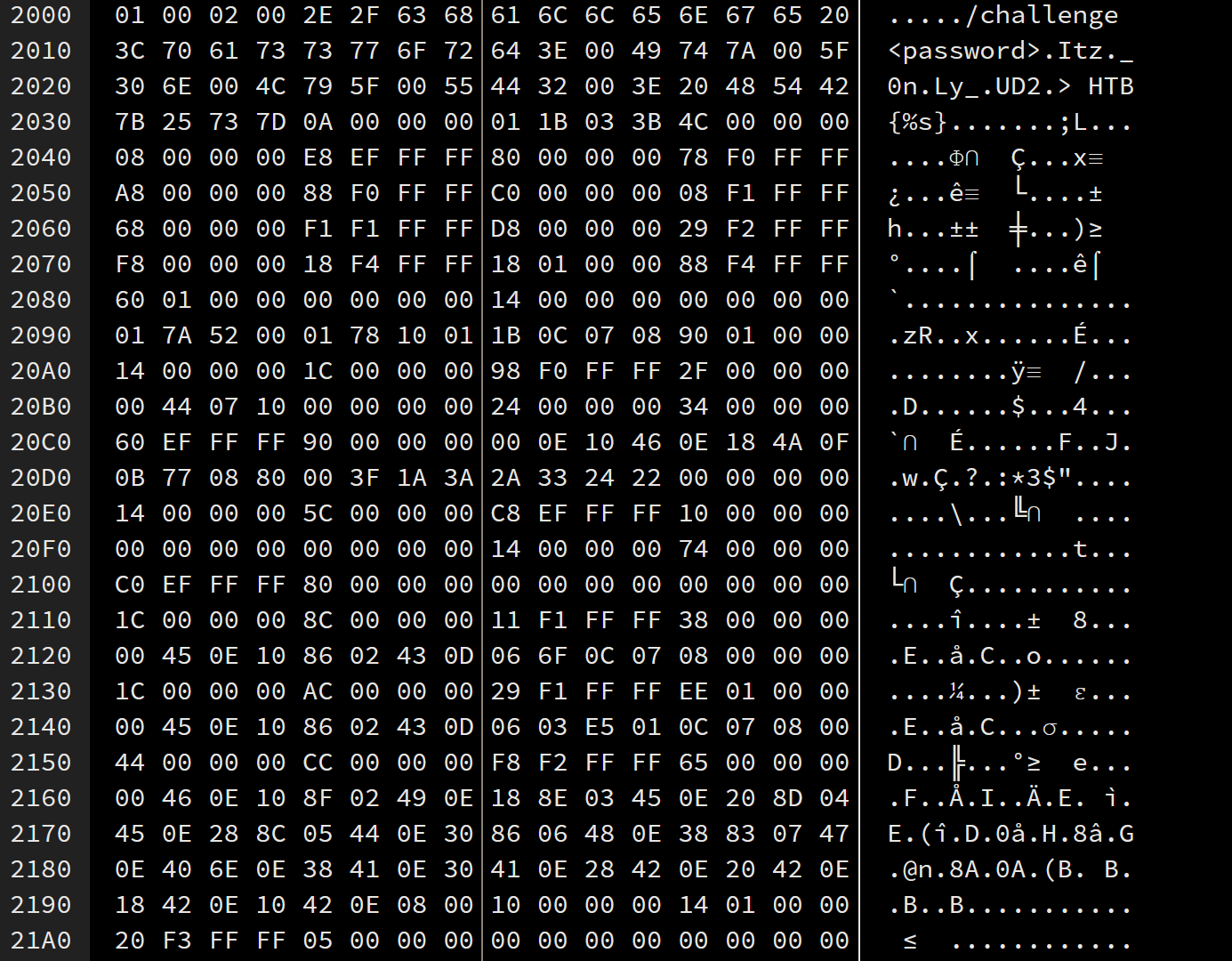
So we need to supply a password to possibly get a flag. Open a Hexviewer or a Debugger of your choice and take a look inside. This is the part I found pretty fast.
Why didn't I just provide the code?
I do not know how to link to a specific part in a program so I will use screenshots for now.
You can see on the lines 2000 through 2010 the output we received when running the program without any arguments/options. After that it says Itz._0n.Ly_.UD2. I am not sure why those dots are there but if you remove them and try to use the cleaned up string Itz_0nLy_UD2 as the password you will get the flag which is basically the same string.
./behindthescenes Itz_0nLy_UD2
> HTB{***********}
This challenge is rather simple if you know what to look for. I saw another writeup where the author reversed the binary further which revealed the function used to compare the string entered to the ‘password’ aka the flag.
Flag
HTB{Itz_0nLy_UD2}